One of the most disregarded happenings in the world of architecture today is that computer networks controlling the buildings and infrastructure architects design are regularly being hacked. This tends to go under-reported, because it often involves private companies concerned for their public images, and untreated, because these systems are coordinated by various parties that have never been responsible for cyber security.
An equally underutilized circumstance is that architects and planners tend to occupy the prime communicating position on building projects, coming into direct or indirect contact with nearly everyone involved. As such, they should familiarize themselves with this realm of knowledge and treat it with equal regard to areas such as structural or mechanical engineering.

Via BBC
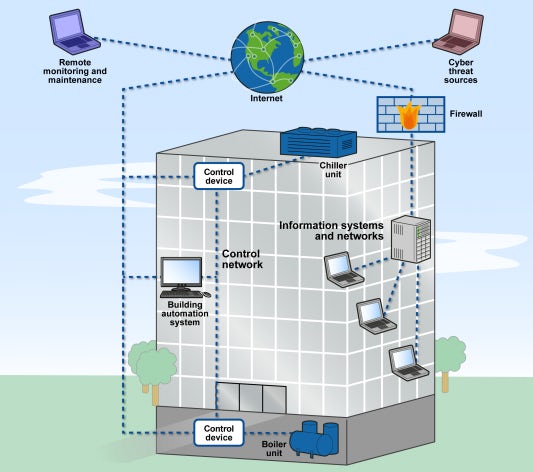
Building automation systems, which control such things as heating and air conditioning, fire alarms and sprinklers, door locks and security cameras, tend to be some of the weakest and least secured computer systems in any given network. The 2013 hack of the retailer Target, for example, in which the credit and debit card information of some 40 million people was stolen, was launched through the company’s heating, ventilation and air conditioning control system.
“The 2013 hack of the retailer Target was launched through the company’s HVAC control system.”
This illustrates why building systems are typically exploited: They’re a weak point through which hackers can jump to an organization’s other systems, like those containing financial data. But as automated buildings become more proliferous and more sophisticated, the range of possible attacks becomes more nefarious. Losing control of the temperature in a hospital or nursing home could be life-threatening; starting a fire by remotely overheating equipment in a building where the fire alarms and sprinklers are intentionally disabled could be catastrophic.
These issues aren’t limited to buildings, as recent hacks have also included the Ukrainian power grid, a small dam in New York and various transportation systems. San Francisco’s BART system has been hacked multiple times, most recently resulting in free rides being given away over Thanksgiving weekend. In that case, only administrative computers were hacked (the ticket-taking machines were intentionally shut down as a precaution), but one doesn’t need too wild an imagination to fear what might happen in a system where automated train controls are compromised.
More significant than potential terrorist acts, though, is the prospect that a transportation system could simply be shut down. Consider the implications if New York City’s five and a half million daily subway riders were unable to get around, crippling the economy of a city with a disproportionately large effect on the gross domestic product of the entire world.
A typical Smart Building setup; via Motherboard
The first step in preventing such problems is to understand, at least on a general level, how these systems work. In the case of buildings, the setup is relatively simple: Physical components that control building systems (a thermostat controlling HVAC, for example) can be accessed remotely by the building’s operators because they’re connected to the internet. In a recent security exercise, for instance, IBM hackers gained access to a large corporation’s building systems through a single Wireless Access Point — a piece of equipment found in most people’s living rooms — and could subsequently control the temperature, fire suppression and security systems in all that company’s buildings across North America.
“Many of these remote connections have no security features to prevent someone else from accessing them.”
Because the vulnerabilities of such systems tend to be overlooked (manufacturers may think that responsibility falls on the IT department, IT may feel it’s out of their purview, etc.) many of these remote connections have no security features to prevent someone else from accessing them. Even when these connections are secured, there tends to be unconsidered weak spots, such as the Wireless Access Point in the IBM exercise, which was guarded with a password stored in an unencrypted list the hackers easily found.
Systems controlling heavy infrastructure are often more complex than off-the-shelf building automation systems. They also tend to be proprietary and customized, so it’s difficult to make generalizations about them, but recent hacking instances illustrate some interesting details. The most documented of these is Stuxnet, in which the centrifuges of nuclear equipment in Iran were purportedly caused to spin themselves into destruction by a worm planted in the the systems of consultant companies that unknowingly carried it into otherwise secure facilities on USB drives.
In this case, the Stuxnet worm illustrates a program’s ability to remain inert and undetected in a system for years, allowing hackers ample time to observe unintelligible processes whose functions can, over time, be deduced by experts. As such, a sophisticated team of hackers and engineers could combine their knowledge to make educated guesses about exactly what equipment is being controlled by lines of code they can see in a network’s everyday functioning, then manipulate it in ways they know would cause damage.

The Bowman Avenue Dam, in Rye Brook, N.Y., was hacked in 2013; via Port Chester Patch
“It is important that architects educate themselves about how a building’s operation will matter in a more connected future — because that future is arriving quickly.”
What can be done about this? The most effective answer lies in the problem: a lack of awareness about these vulnerabilities. Automated building systems control equipment that works in essentially the same way since well before the digital revolution. This equipment is engineered, designed, manufactured and installed by a chain of people who likely have no knowledge, expertise or training in cyber security.
The good news is that an architect (in close quarters with a construction contractor or manager) is typically the conduit through which all these parties communicate with each other. Thus, if architects were to treat knowledge of these weaknesses the same way they treat knowledge of the building equipment that contains them, they could help spread that awareness to everyone involved in a project — a vital first step in making safeguards against hacking a standard practice.
It’s most likely that the security of building and infrastructure controls will eventually fall to the responsibility of a single-source expert, in much the same way that structural or mechanical engineering is handled today. But that is a nascent field, and when it does take on a greater role in building projects, architects and planners will undoubtedly be tasked with coordinating that person’s involvement, as well. In the meantime, it is important that architects educate themselves as much as possible about how a building’s operation will matter in a more connected future — because that future is arriving quickly.
Top image via Security Intelligence









